Nygma Cloud Zero-Knowledge Encryption: The Math Behind True Privacy on International Computer Security Day
Every year, International Computer Security Day (November 30) reminds individuals and organizations of a rapidly growing truth: modern cloud systems still require you to trust the provider with access to your data.
Most major cloud platforms encrypt your files—yet they keep the keys. That means they can read your content, scan it, hand it over under legal compulsion, or expose it in a breach. This is not a hypothetical problem. Provider-side access is the central flaw of traditional cloud storage architectures.
Nygma Cloud solves this by removing trust from the equation entirely. Its zero-knowledge encryption architecture means the provider is mathematically, architecturally, and cryptographically incapable of accessing your files—even if compelled.
Today, we celebrate International Computer Security Day by examining how Nygma converts privacy from a promise into a provable mathematical guarantee—and why this matters for lawyers, journalists, researchers, and anyone handling sensitive information.
The Problem with “Encrypted” Cloud Storage: Trust-Based Security
Traditional cloud storage encrypts your files—but the encryption is typically server-side, meaning the provider:
- Generates or stores the encryption keys
- Can decrypt your content at any time
- Reads metadata (filenames, folder names, timestamps, structure)
- Can be compelled legally to hand everything over in human-readable form
- Often scans content for “feature enhancements,” ads, or AI-based processing
These models place users in a vulnerable position—dependent on policies rather than provable protections.
The Nygma Whitepaper captures the issue clearly:
“Policy-based security says ‘we won’t look at your data.’
Technical security says ‘we cannot look at your data.’”
On International Computer Security Day, this distinction is the heart of the conversation.
Zero-Knowledge Encryption: Privacy Guaranteed by Mathematics
🔒 What Zero-Knowledge Encryption Actually Means
Nygma Cloud implements true zero-knowledge encryption based on four strict principles:
- Client-side encryption:
All encryption happens before data leaves your device. - No key transmission:
Nygma never receives your password or the derived encryption keys. - Metadata encryption:
Even filenames, folder names, and timestamps are encrypted, leaving no breadcrumbs behind. - No backdoors, no recovery mechanism on the server:
Password resets are cryptographically impossible; only your recovery key can unlock data.
This model doesn’t just prevent unauthorized access—It makes access mathematically impossible.
The Mathematics Behind Nygma’s Zero-Knowledge System
☑️ Strong Cryptography at Every Layer
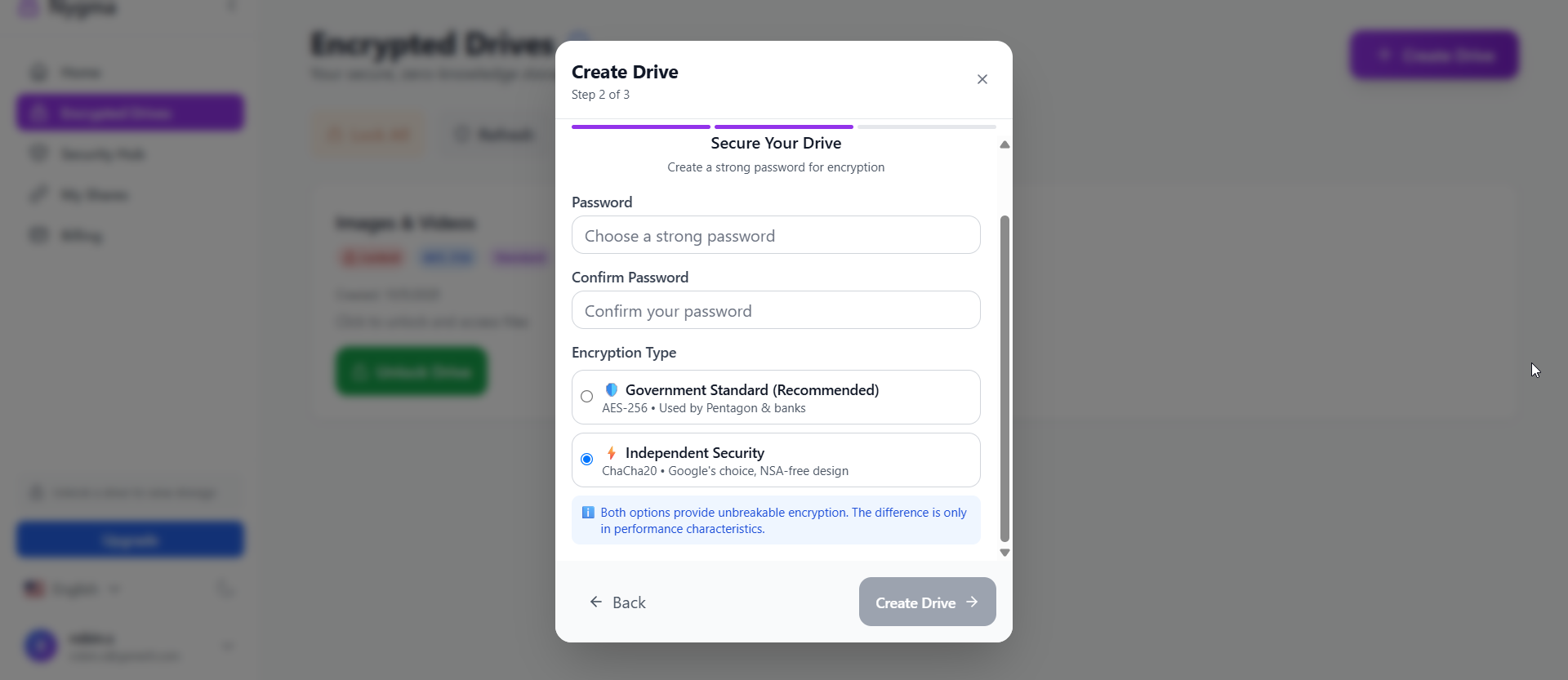
Nygma offers a multi-tier encryption system built on audited, modern cryptographic algorithms:
- AES-256-GCM (Nygma Shield) — military-grade encryption
- ChaCha20-Poly1305 (Quantum Shield) — exceptional performance on mobile hardware
- Multi-layer encryption (Paranoid Shield) — AES + ChaCha20 stacking for maximum defense
These ciphers are mathematically resistant to brute force. AES-256 alone would require billions of years for a supercomputer to break through randomized key space.
☑️ Hierarchical Keys Derived on Your Device
Nygma uses a tiered cryptographic key hierarchy:
- Master Key (derived from your password via PBKDF2, 100,000+ iterations)
- Content Key
- Metadata Key
- Recovery Key (24-word BIP-39 mnemonic)
Nygma never stores the Master Key and never receives the password. All files, folders, thumbnails, and metadata are encrypted locally using these keys.
☑️ Authentication Without Ever Seeing Your Password
To verify password correctness without receiving it, Nygma encrypts random verification data during setup. During login, only your local device can perform the correct decryption.
It’s mathematically impossible for the provider to guess or reconstruct your keys.
Why Zero-Knowledge Matters for Real Professionals
International Computer Security Day isn’t just about awareness—it’s about protecting the real people whose livelihoods depend on privacy.
✅ Lawyers
Legal teams depend on confidentiality. Zero-knowledge encryption enforces attorney-client privilege at a cryptographic level.
- Sensitive case files become mathematically inaccessible
- Discovery documents remain visible only to the correct parties
- Duress Mode protects clients during border crossings or coercive searches
✅ Journalists & Investigators
For journalists working in hostile or high-risk regions:
- Sources cannot be exposed
- Research files remain invisible to cloud providers, governments, or attackers
- The Time Bomb auto-delete system protects data if a device is confiscated
✅ Academic & Scientific Researchers
Unpublished research carries tremendous value. Zero-knowledge encryption:
- Protects lab notebooks, datasets, prototypes, IP
- Prevents insider threats and industrial espionage
- Allows secure, selective sharing using Nygma’s URL-fragment sharing system
These examples show why zero-knowledge encryption isn’t niche—it’s essential.
Beyond Encryption: Nygma’s Advanced Privacy Protections
🗝️ Metadata Encryption
Traditional encrypted clouds still expose filenames like: “Contract_Draft_January2025.docx”
Nygma encrypts even filenames, folder names, sizes, timestamps, and directory structure.
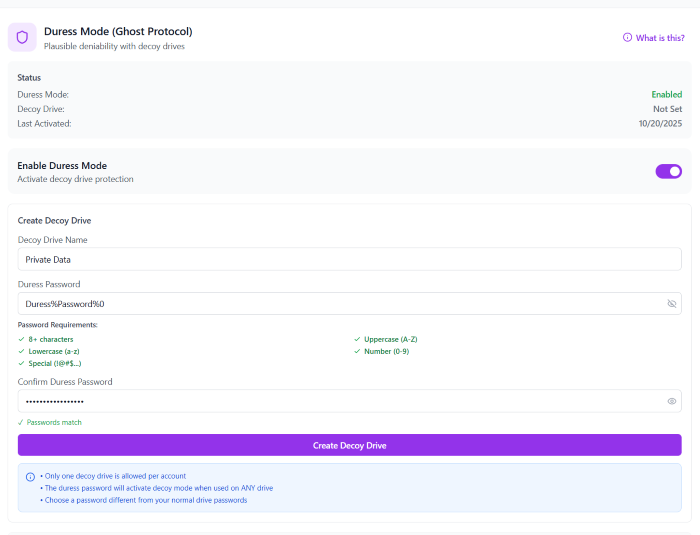
🗝️ Duress Password System
If forced to unlock your cloud:
- A duress password safely opens a decoy drive
- Real content remains protected
- The system behaves normally, providing true plausible deniability
🔗 Duress Mode (Ghost Protocol) with Nygma Cloud
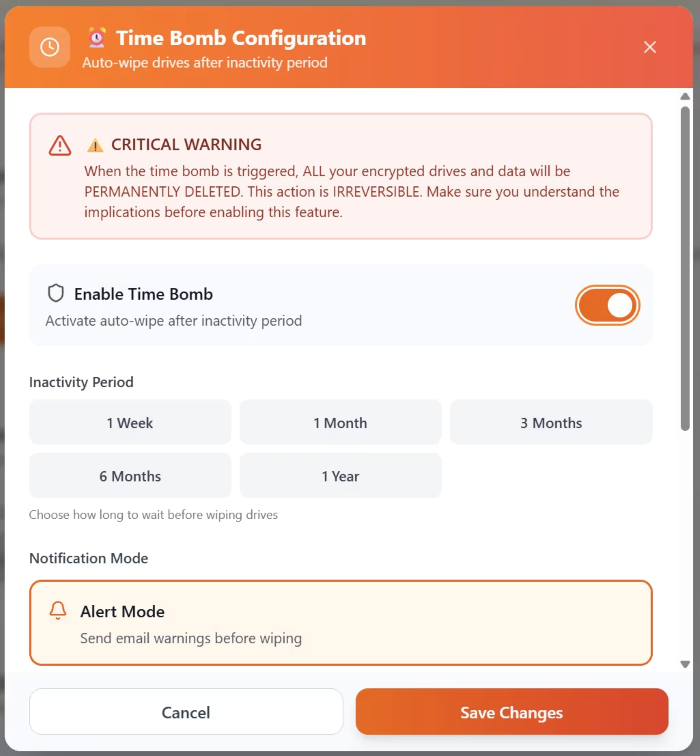
🗝️ The Time Bomb Feature
For forgotten devices or long-term inactivity:
- Drives auto-lock
- Keys wipe from memory
- Optional full data destruction after prolonged inactivity
🔗 Time Bomb: Auto-Delete on Inactivity
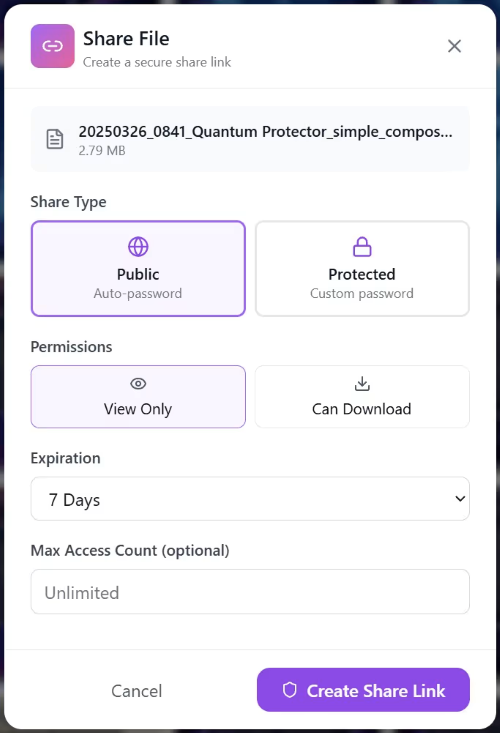
🗝️ Zero-Knowledge Sharing
Nygma uses URL fragment sharing, where the encryption key is passed only in the “#” part of the URL—never sent to a server.
This creates true end-to-end encrypted sharing.
Ready to experience mathematically guaranteed privacy?
Modern Security Should Require Zero Trust—Literally
The world is moving toward systems where trust is not a prerequisite for use. Zero-knowledge encryption is the foundation for that future.
Nygma’s zero-knowledge architecture means:
- A data breach exposes only encrypted blobs
- Legal requests yield only encrypted blobs
- Insider threats see only encrypted blobs
- Server compromise results in… only encrypted blobs
Privacy is no longer a matter of policy—it’s a function of math.
On International Computer Security Day, the message is simple: If the provider can access your data, it’s not private.
Embrace True Digital Privacy with Nygma Cloud
Nygma represents the next generation of cloud security—backed by technical rigor, real cryptography, and a privacy model designed for the modern world.
If you are celebrating International Computer Security Day by improving your digital security posture, start with the solution that delivers mathematical privacy.
FAQs
❓ What makes zero-knowledge encryption different from normal encryption?
Normal encryption gives the provider access to encryption keys. Zero-knowledge encryption ensures encryption keys never leave your device, making provider access impossible.
❓ Can Nygma employees access my files?
Technically impossible. Nygma never holds your encryption keys or plaintext metadata.
❓ What if I lose my password?
Only your recovery key (24-word phrase) can regenerate your Drive Keys.
❓ How does sharing work if the provider cannot decrypt files?
Nygma uses URL-fragment key sharing, where the decryption key is transmitted only via the part of the URL not visible to the server.
❓ Is Nygma suitable for professional use (legal, research, journalism)?
Yes. Its zero-knowledge architecture and advanced systems like Duress Mode and Time Bomb are specifically valuable for high-risk professions.