New Year Cybersecurity Resolutions With Nygma Cloud
As individuals and organizations set strategic goals for the new year, cybersecurity should be a central priority. The growing volume of sensitive data stored and shared digitally has made robust security practices essential—not optional. Data breaches, ransomware incidents, and identity theft continue to rise globally, emphasizing the need for long-term, sustainable digital protection strategies.
This article outlines practical cybersecurity resolutions and explains how Nygma Cloud supports these goals through a privacy-first, zero-knowledge security architecture designed for modern digital life.
Prioritizing Cybersecurity as a Long-Term Habit
Cybersecurity is most effective when treated as an ongoing discipline rather than a reactive measure. Establishing consistent security habits—such as encrypted storage, controlled sharing, and regular backups—significantly reduces exposure to digital threats.
Nygma Cloud is designed to support this approach by embedding security at every stage of the data lifecycle, from creation to sharing and long-term storage.
Resolution 1: Adopt Zero-Knowledge Encrypted Cloud Storage
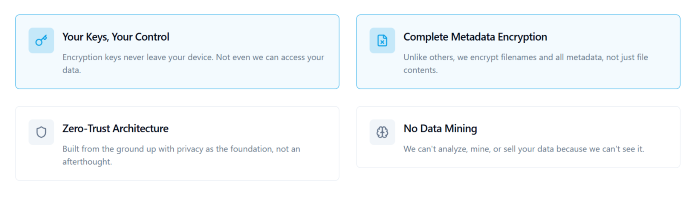
One of the most impactful cybersecurity decisions is selecting a cloud storage solution that enforces zero-knowledge encryption. With this model, data is encrypted locally before it is uploaded, and encryption keys remain exclusively under the user’s control.
Nygma Cloud applies client-side encryption to all stored data, ensuring that:
- Files are unreadable to third parties
- Metadata such as filenames remains encrypted
- Even the service provider cannot access user content
This architecture significantly reduces the risk associated with insider threats, unauthorized access, and external breaches.
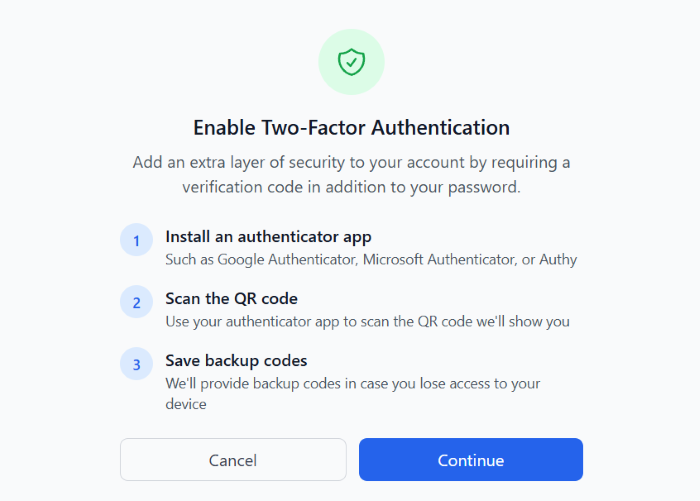
Resolution 2: Strengthen Account Protection With Multi-Factor Authentication
Passwords alone are no longer sufficient to protect sensitive accounts. Multi-factor authentication (MFA) adds an essential second layer of verification, dramatically reducing the success rate of credential-based attacks.
Industry research indicates that MFA can prevent the majority of automated account compromise attempts when properly implemented.
Nygma Cloud supports strong authentication mechanisms to help users protect access to encrypted drives and shared data.
Resolution 3: Minimize Sensitive Data Stored on Local Devices
Storing confidential documents on laptops, mobile phones, or external drives increases exposure to loss, theft, and malware infections. A cybersecurity-focused approach involves reducing local storage of sensitive files and relying instead on encrypted cloud environments.
By centralizing sensitive data within an encrypted Nygma Cloud drive, users can:
- Reduce risk from stolen or compromised devices
- Maintain secure access across multiple devices
- Ensure consistent protection regardless of location
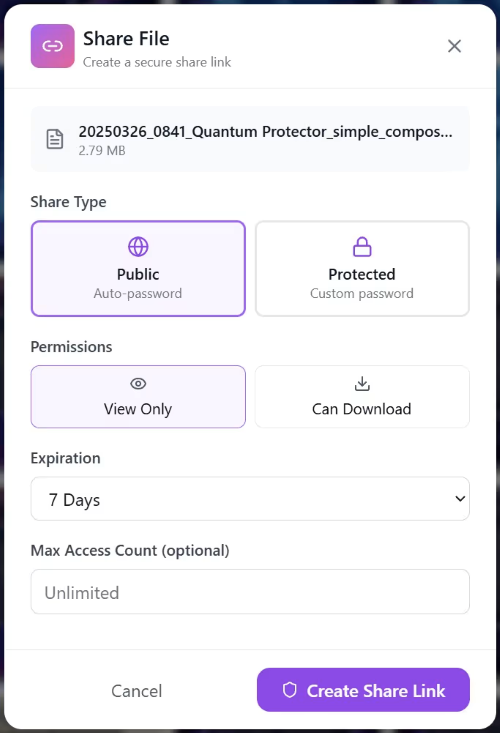
Resolution 4: Implement Controlled and Secure File Sharing
Unrestricted file sharing is a common source of data exposure. Effective cybersecurity includes enforcing access controls and limiting file availability based on necessity.
Nygma Cloud’s advanced sharing features allow users to:
✅Apply password protection to shared files
✅Define expiration dates for access
✅Control download and viewing permissions
These measures ensure that sensitive information is shared only with intended recipients and only for the required duration.
Resolution 5: Establish a Consistent and Sustainable Backup Rhythm
Regular backups remain a fundamental component of cybersecurity resilience. Hardware failures, accidental deletions, and ransomware incidents can result in irreversible data loss without a reliable backup strategy.
A recommended approach includes:
📌Scheduled backups of critical data
📌Secure storage of backup copies in encrypted environments
📌Periodic review and validation of backup integrity
Combining disciplined backup routines with encrypted cloud storage provides a strong defense against both cyber threats and operational disruptions.
Why These Cybersecurity Resolutions Matter
According to the Identity Theft Resource Center, data breach incidents continue to affect millions of individuals annually, exposing personal and financial information. These trends underscore the importance of proactive cybersecurity planning rather than reactive remediation.
Adopting structured security habits supported by technologies such as zero-knowledge encryption and secure sharing can significantly reduce long-term risk.
❓FAQ
What is zero-knowledge encryption?
It is a security model where data is encrypted before upload, and only the user controls the encryption keys, ensuring complete privacy.
How does secure sharing improve cybersecurity?
It limits unauthorized access by enforcing permissions, passwords, and expiration rules for shared content.
Is cloud storage safer than local storage?
When combined with client-side encryption and strong authentication, encrypted cloud storage is often safer than storing sensitive files locally.
How often should backups be performed?
Backup frequency should align with how often data changes—weekly for personal use and more frequently for business-critical data.
Moving Forward With Stronger Cybersecurity
Cybersecurity is not a single resolution—it is an ongoing commitment. By adopting encrypted storage, strengthening authentication, controlling data sharing, and maintaining reliable backups, users can significantly improve their digital security posture.
Nygma Cloud supports these objectives through a privacy-first, zero-knowledge architecture designed to protect data today and in the years ahead.